Windows Vulnerability Alert - CVE-2025-21298: A Severe Zero-Click Vulnerability in Windows OLE
CVE-2025-21298 is a critical zero-click vulnerability in Windows OLE that allows attackers to execute malicious actions without user interaction, potentially compromising system security.
2/7/20252 min read


In January 2025, a critical security vulnerability, CVE-2025-21298, was revealed, impacting Windows Object Linking and Embedding (OLE) technology. With a CVSS score of 9.8, this flaw enables remote code execution (RCE) via specially crafted emails, presenting serious risks to both users and organizations.
Understanding the Vulnerability
The vulnerability is located in the ole32.dll library, specifically within the UtOlePresStmToContentsStm function. This function handles the conversion of data in an "OlePres" stream within OLE storage, formatting it correctly and inserting it into the "CONTENTS" stream of the same storage.
A proof of concept (PoC) for CVE-2025-21298 has been released on GitHub, showcasing the memory corruption issue that triggers this vulnerability.
Steps to Reproduce
Open up a new word instance:
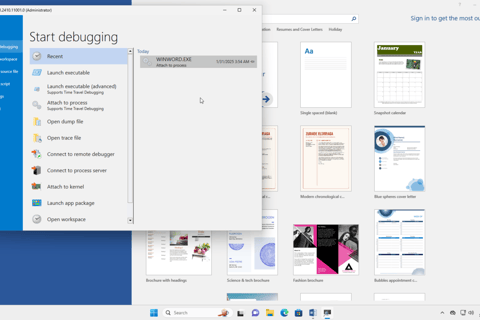
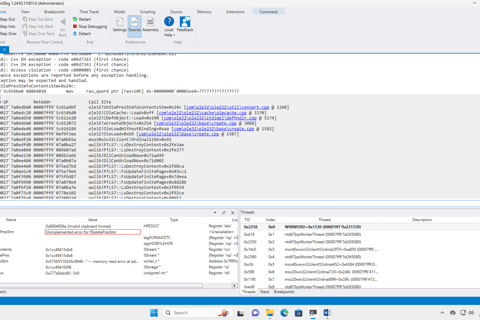
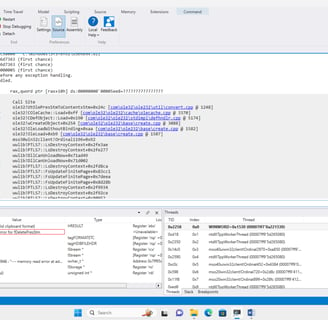
Attach WinDbg to the running WINWORD.EXE process:
Open up the poc.rtf given in the repository and you will see WORD being crashed:
Impact
If successfully exploited, attackers can acquire the same privileges as the current user, potentially resulting in complete system compromise.
This includes the ability to:
Install programs
View, change, or delete data
Create new accounts with full user rights
The zero-click nature of this vulnerability allows exploitation to occur without any user interaction other than opening or previewing the malicious email, which significantly heightens its severity.
Prevention and Suggested Actions
Microsoft has issued patches to resolve this vulnerability in the January 2025 Patch Tuesday updates.
Users and organizations are highly encouraged to apply these updates as soon as possible to minimize potential risks.
For those unable to update right away, a suggested workaround is to configure Outlook to display all standard emails in plain text format, lowering the likelihood of automatic exploitation.
Conclusion
CVE-2025-21298 poses a major security risk due to its high severity and the ability for remote code execution without user interaction.
Promptly applying patches and implementing recommended workarounds is crucial to safeguarding systems from potential exploitation.
Ongoing monitoring and the use of detection rules can further strengthen an organization’s defenses against such vulnerabilities.
Credits: Offsec
Thanks for reading!
To learn more about our services and how we can help protect your systems, visit https://www.vaptern.com/services or contact us directly.