Pwn2Own Automotive 2025: Hackers Win Massive $886,250 Bounty
49 Zero-Days Exploited: Hackers Reap $886,250 at Pwn2Own Automotive 2025
1/24/20252 min read
The Pwn2Own Automotive 2025 hacking contest has concluded, with security researchers earning $886,250 after exploiting 49 zero-day vulnerabilities.
During the event, they focused on automotive software and products, such as electric vehicle (EV) chargers, car operating systems like Android Automotive OS, Automotive Grade Linux, and BlackBerry QNX, as well as in-vehicle infotainment (IVI) systems.
As per the Pwn2Own Tokyo 2025 contest rules, all targeted devices were running the latest operating system versions and had all available security updates applied.
Although Tesla provided a Model 3/Y (Ryzen-based) equivalent benchtop unit, security researchers participating in the competition only attempted exploits against the company’s Wall Connector charger.
The competitors earned $382,750 in cash prizes after demonstrating 16 unique zero-day vulnerabilities on the first day. On the second day, they collected an additional $335,500 after exploiting 23 more zero-days and hacking Tesla’s EV charger twice. On the third day of Pwn2Own, they earned another $168,000 for demonstrating 10 more zero-day vulnerabilities.
Once the zero-days are demonstrated and reported during Pwn2Own events, vendors have 90 days to release security patches before TrendMicro's Zero Day Initiative discloses them publicly.
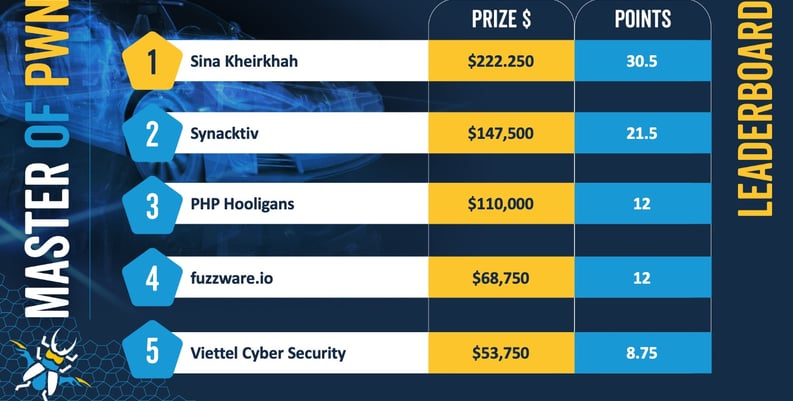
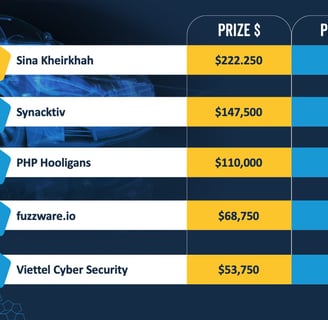
Sina Kheirkhah from Summoning Team won the Pwn2Own Automotive 2025 competition this year, earning 30.5 Master of Pwn points and $222,250 in cash prizes for hacking multiple EV chargers and In-Vehicle Infotainment (IVI) systems.
Synacktiv claimed second place with $147,500, PHP Hooligans earned $110,000, fuzzware.io walked away with $68,750, and Viettel Cyber Security took home $53,750 for the zero-day exploits demonstrated over the three days of the competition.
You can find the results for each challenge on the final day of Pwn2Own Automotive 2025, as well as the overall results, here.
In the first Pwn2Own Automotive event in January 2024, security researchers earned $1,323,750 by demonstrating 49 zero-day vulnerabilities in various electric car systems and hacking a Tesla car twice.
Just two months later, at Pwn2Own Vancouver 2024, ZDI awarded another $1,132,500 for 29 zero-day exploits. Synacktiv walked away with $200,000 and a Tesla Model 3 after hacking its ECU with Vehicle (VEH) CAN BUS Control in under 30 seconds.
