Palo Alto Networks Fixes Authentication Bypass Vulnerability in PAN-OS Software
Palo Alto Networks Fixes Authentication Bypass Vulnerability in PAN-OS Software
2/13/20252 min read
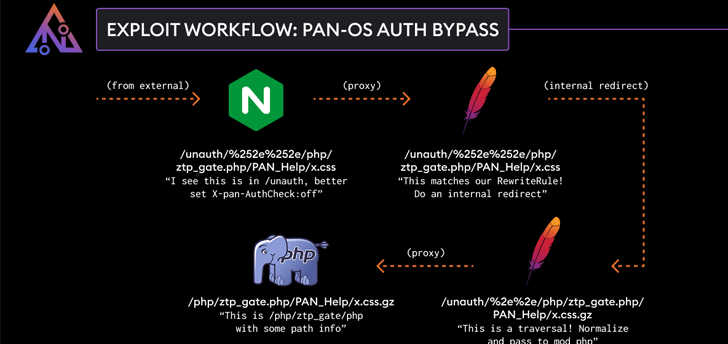
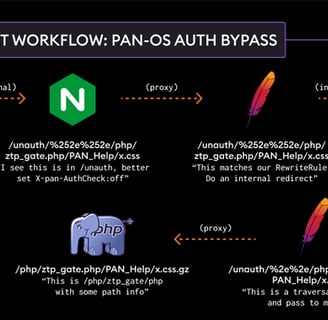
Palo Alto Networks has patched a high-severity security vulnerability in its PAN-OS software that could lead to an authentication bypass.
The flaw, identified as CVE-2025-0108, has a CVSS score of 7.8 out of 10.0. However, if access to the management interface is limited to a jump box, the score drops to 5.1.
According to Palo Alto Networks' advisory, "An authentication bypass in the PAN-OS software allows an unauthenticated attacker with network access to the management web interface to bypass the required authentication and invoke specific PHP scripts."
"Although executing these PHP scripts does not enable remote code execution, it can undermine the integrity and confidentiality of PAN-OS."
The vulnerability affects the following versions -
PAN-OS 11.2 < 11.2.4-h4 (Fixed in >= 11.2.4-h4)
PAN-OS 11.1 < 11.1.6-h1 (Fixed in >= 11.1.6-h1)
PAN-OS 11.0 (Upgrade to a supported fixed version as it has reached end-of-life status on November 17, 2024)
PAN-OS 10.2 < 10.2.13-h3 (Fixed in >= 10.2.13-h3
PAN-OS 10.1 < 10.1.14-h9 (Fixed in >= 10.1.14-h9)
Adam Kues, a security researcher at Searchlight Cyber/Assetnote, who is credited with discovering and reporting the vulnerability, explained that the flaw stems from a discrepancy in how the Nginx and Apache components of the interface handle incoming requests, leading to a directory traversal attack.
Palo Alto Networks has also released updates to fix two additional vulnerabilities:
CVE-2025-0109 (CVSS score: 5.5) – An unauthenticated file deletion vulnerability in the PAN-OS management web interface, which allows an attacker with network access to delete certain files as the "nobody" user, including limited logs and configuration files. (Fixed in PAN-OS versions 11.2.4-h4, 11.1.6-h1, 10.2.13-h3, and 10.1.14-h9)
CVE-2025-0110 (CVSS score: 7.3) – A command injection vulnerability in the PAN-OS OpenConfig plugin, which allows an authenticated administrator who can make gNMI requests to the PAN-OS management web interface to bypass system restrictions and execute arbitrary commands. (Fixed in PAN-OS OpenConfig Plugin version 2.1.2)
To reduce the risk from these vulnerabilities, it is strongly recommended to disable access to the management interface from the internet or any untrusted network. Customers who do not use OpenConfig should consider disabling or uninstalling the plugin from their instances.
To learn more about our services and how we can help protect your systems, visit https://www.vaptern.com/services or contact us directly.
